IT leaders that already know the benefit of VDI may see the need to scale their existing environment but are hesitant to begin the process because of budget restrictions. And they are right in being wary of a complete overhaul of their existing hardware. High performing endpoints can cost a fortune, and amidst the horizon of rapidly growing demands on time and budget, organizations must find better ways to manage and scale their environments, while at the same time cut back strain on staff who are left with more work than they can achieve alone.
With VDI, any given organization’s productivity depends greatly on how well system administrators can effectively manage their entire network of mixed endpoint devices, and deliver virtual desktops, applications, and necessary information to their end users in a convenient and expedient way. For this reason, organizations cannot afford to overlook this important aspect of their business. Endpoint management can, for better or for worse, have a disproportionate impact on the overall well-being of day-to-day operations.
Stratodesk Adds an Important Security Layer to Endpoint Devices
Stratodesk NoTouch is a highly secure software solution. User interaction with the system is limited to (unless otherwise configured) clicking on an icon, entering username & password, and then being taken into a full-screen remote desktop. There are not many services running that allow access from the network. The default installation includes several features that may be of interest to some but are not strictly necessary, and services like SSH are turned off by default. It’s also possible to prevent USB storage devices from being mounted to the OS let alone be forwarded to a virtual desktop environment.
Stratodesk NoTouch is a Linux based operating system, which means that it is impervious to common security threats that target or exploit x86 and ARM based devices.
No Personal Data is Stored
Devices powered by Stratodesk NoTouch do not store any personal data on the endpoints themselves. Furthermore, Stratodesk also protects against the possibility of confidential data or information being acquired when a device is lost or stolen. Stratodesk NoTouch does this by safeguarding critical, sensitive information by encrypting it and blocking access to it. And while this form of encryption is very effective, some companies will inevitably require further and even more extensive security for certain information deemed by most to be not worthy of protection. For such companies, we offer a Disk Encryption upgrade.
Disk Encryption for Added Protection
Stratodesk’s Disk Encryption can transparently encrypt the writable portion of the local storage medium on client devices where Stratodesk NoTouch is deployed. This means that in case of a device being stolen or illegitimately accessed, the data cannot be read. Disk Encryption can easily be switched on or off from Stratodesk NoTouch Center and can allow for two different key phrases: one from the system, and one inputted by the user, although for increased security we’d recommend the user input method as this requires them to enter a boot password before it will boot to the desktop so works in a similar way to Microsoft’s BitLocker.
Even in VDI deployments where most personal information is not stored on the endpoint device itself, with Disk Encryption, any additional data, including URLs or private network certificates, will also be encrypted. Stratodesk protects all vital information from being physically accessed by unauthorized users and offers Disk Encryption to encrypt all data on the writable portion of the disk.
How to Enable Disk Encryption
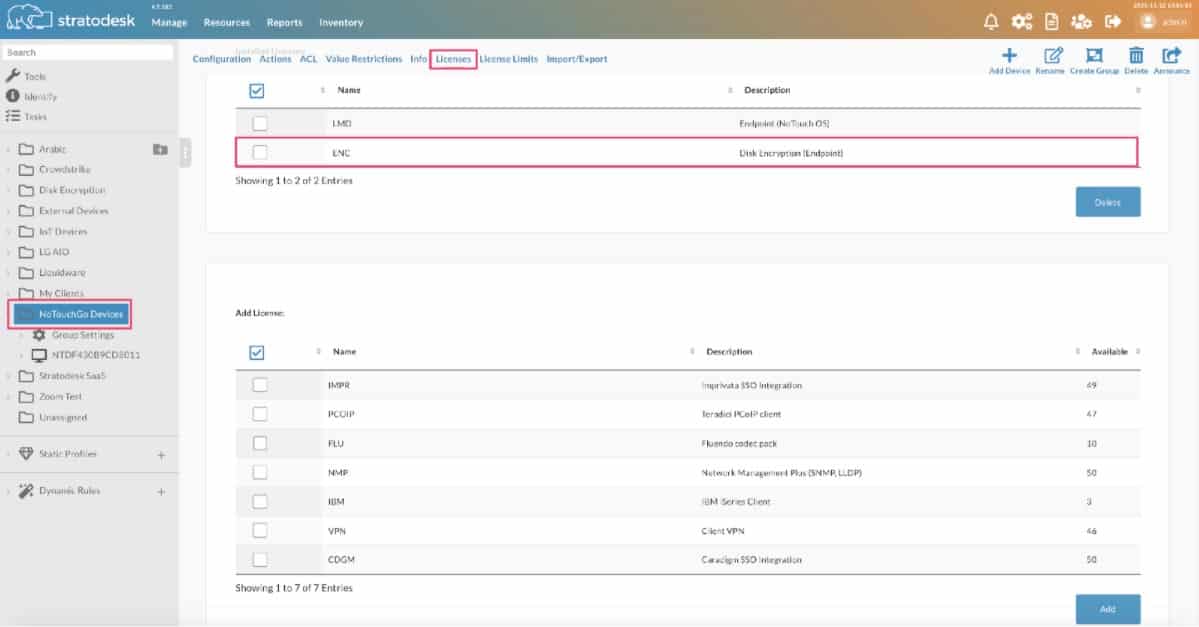
Disk encryption is a premium add-on so devices must have a licence to use this feature. This licence can be applied to a group of devices or to a device itself as shown below.
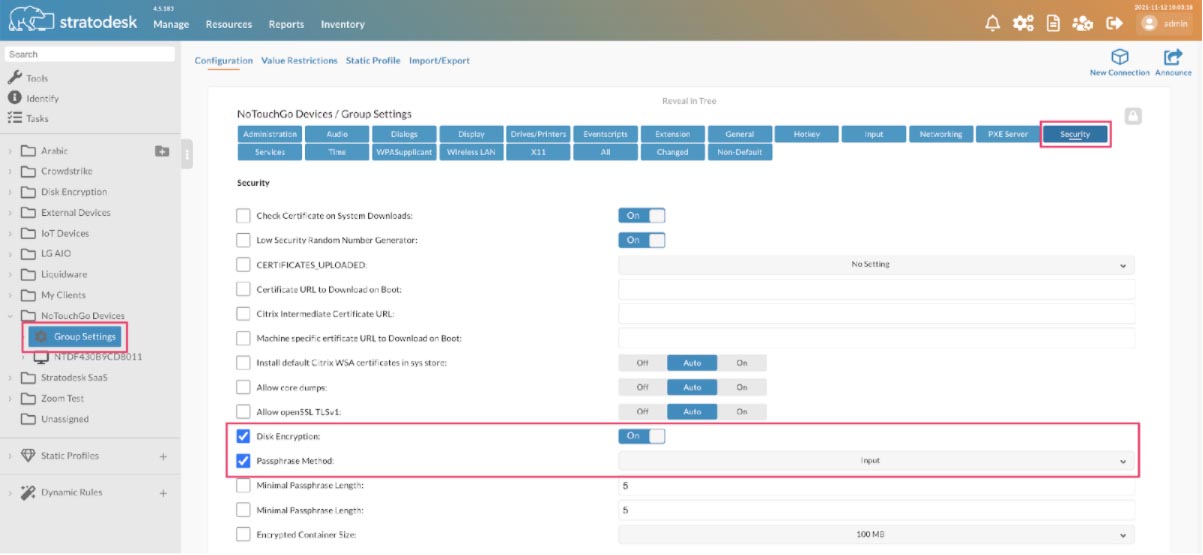
You will also need to configure the disk encryption service which is done in ‘Security’ group settings. The service needs to be enabled and the ‘Passphrase Method’ should be chosen.
- System – The system will create its own password and the device will automatically boot into Stratodesk NoTouch OS.
- Input – This is where the user will create their own password onto the next reboot of the device and is more secure as the device will not boot unless the password has been entered.
What does this look like on the drive?
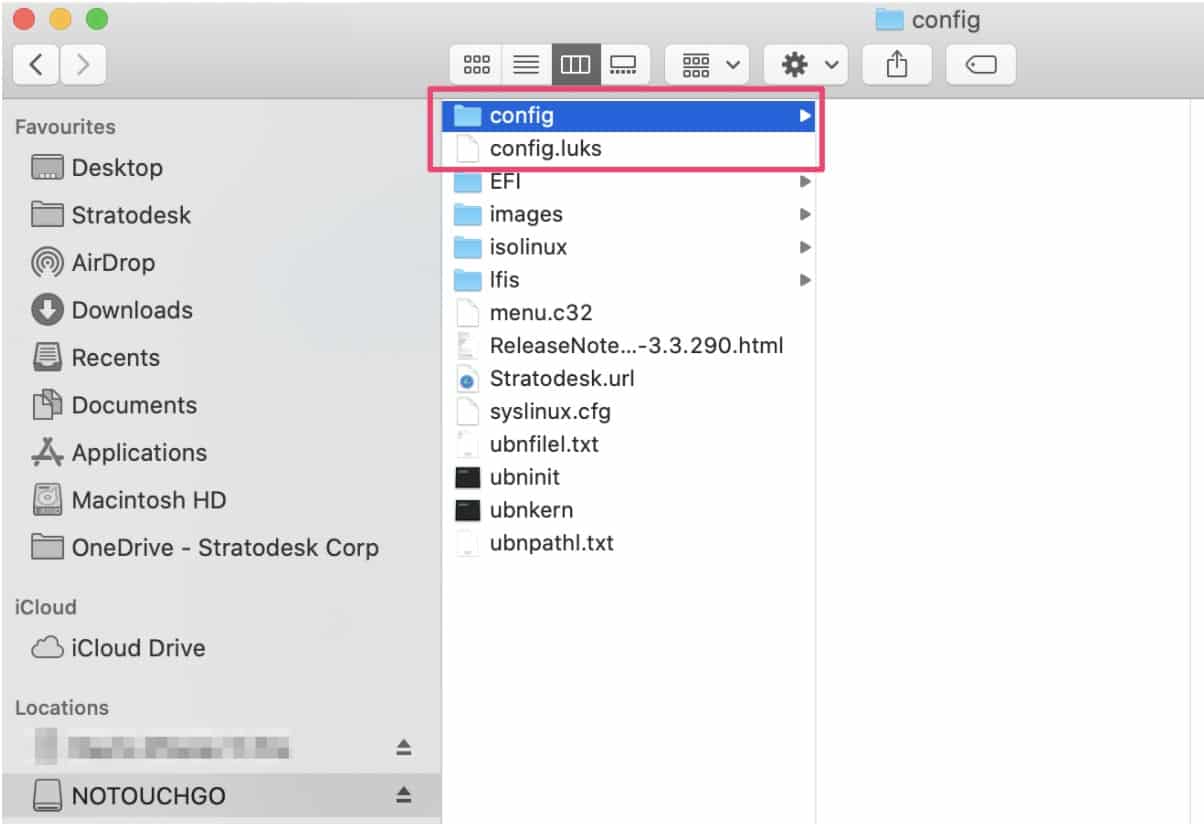
The example below is taken from a Stratodesk NoTouch GO USB drive, but note that the config directory is empty, and instead the configuration is encrypted in the config.luks file.
Additional information on disk encryption can be found in the following knowledge base article.
As such disk encryption is a great feature for devices like laptops, Stratodesk NoTouch GO or USB devices that have the potential to be lost or stolen or even if your security policies dictate that all devices must be capable of being encrypted.
One point of note when using disc encryption, it’s not recommended that you use configuration preload as this requires both the config.cfg & live.cfg files to be placed outside the encrypted config directory, and therefore can be easily read.
Crowdstrike
Whilst Stratodesk NoTouch OS is an incredibly secure Linux operating system, due to existing security policies many organisations still require some form of anti-virus & malware protection on their Stratodesk NoTouch based VDI endpoints. Typically, antivirus solutions can be resource heavy which can cause performance issues on some low specification devices like thin clients.
One way to overcome this is with Crowdstrike Falcon which is a next generation cloud-based anti-virus solution that uses a lightweight agent that is unobtrusive in nature and has a minimal impact on the endpoint. Stratodesk has partnered up with Crowdstrike to bring their next generation anti-virus protection to VDI Thin Client endpoints.
The good news for Stratodesk customers is that we make the deployment and configuration of the Crowdstrike sensor incredibly easy.
How to configure Crowdstrike Falcon in Stratodesk NoTouch
Getting Started
- Log into your Crowdstrike environment and download the Crowdstrike Sensor as shown below.
- Download the Crowdstrike Ubuntu sensor.
- Make a note of your Customer ID, as this is needed when enabling the Crowdstrike service in Stratodesk NoTouch Center.
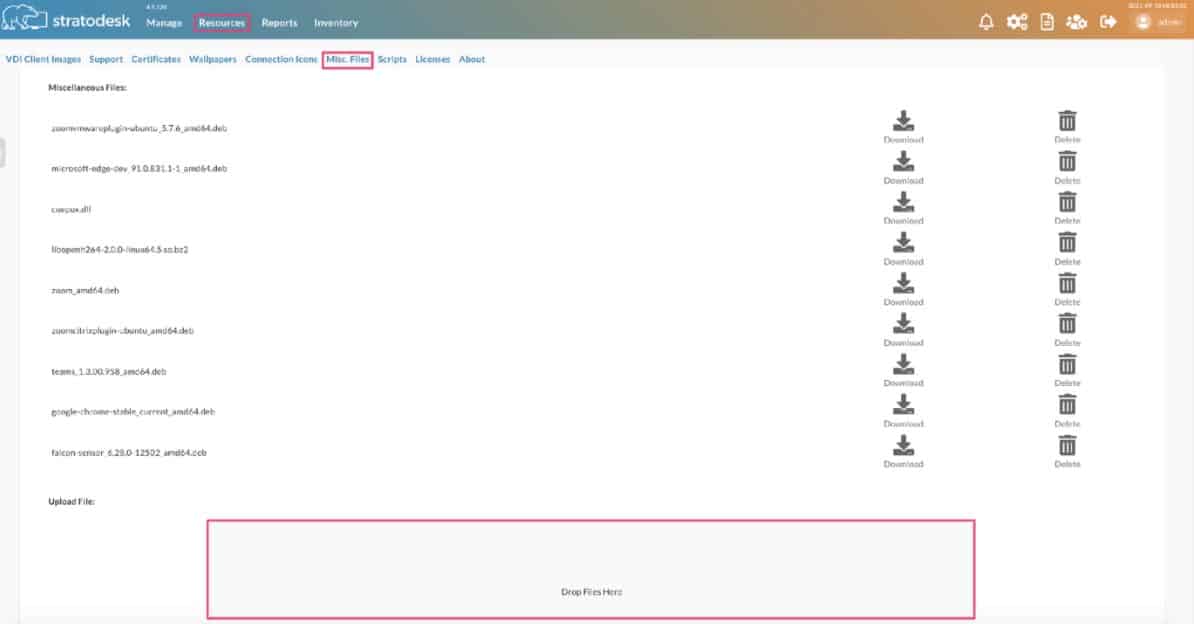
- Next log into Stratodesk NoTouch Center and go to ‘Resources/Misc.Files’ and upload the Falcon-Sensor, as Stratodesk NoTouch Center will become the distribution point to your Stratodesk NoTouch OS endpoints.
- To configure the Crowdstrike service & Customer ID go to ‘Group Settings/Services’ and enable the service and copy the Customer ID into the ‘CCID’ field.

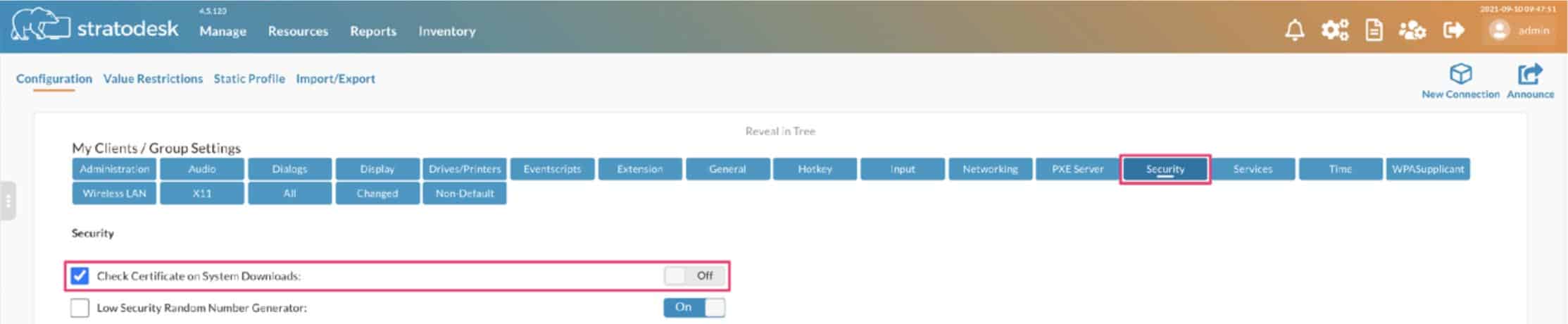
- If your Stratodesk NoTouch Center is using a self-signed certificate, then go to the ‘Group Settings/Security’ and disable the ‘Check Certificates on System Downloads’ parameter.
- Once complete announce the change, and then reboot the Stratodesk NoTouch OS endpoint.
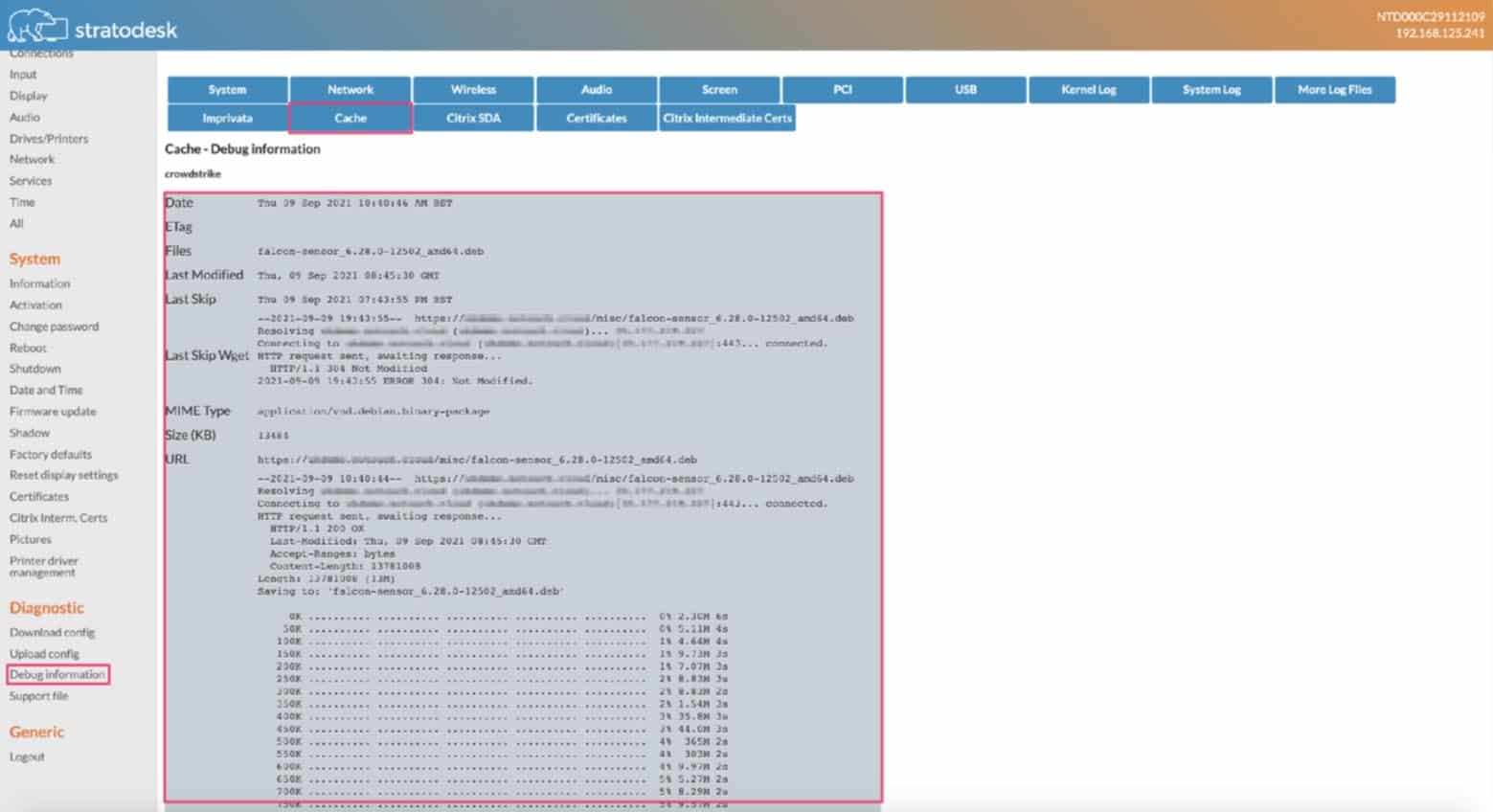
- To verify the installation has been successful, log into the local configuration of the endpoint, and then go to ‘Debug Information/Cache’ to ensure the download of the sensor has been successful.
- The final step is to log into ‘Hosts-Overview’ of the Crowdstrike dashboard to check that the Stratodesk NoTouch OS endpoints show under Linux hosts and are correctly connected.
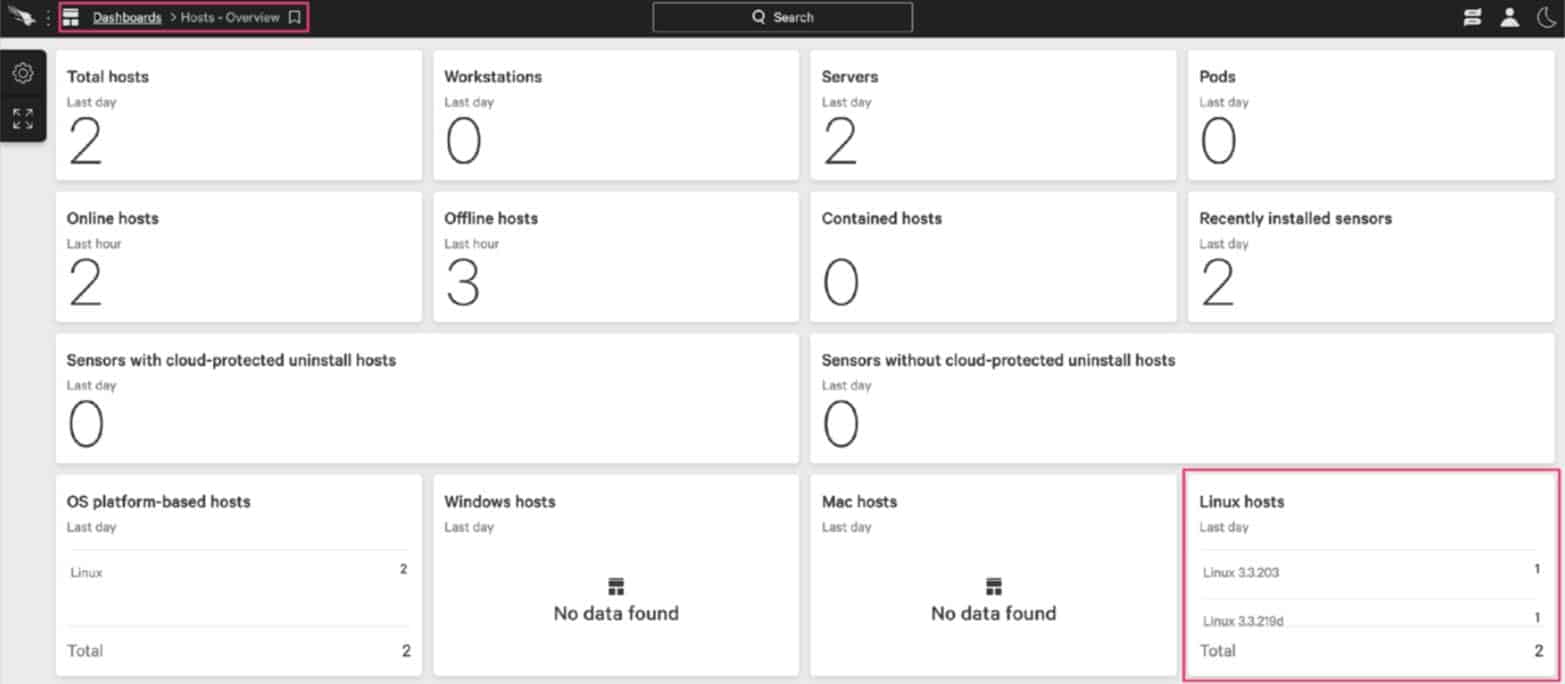
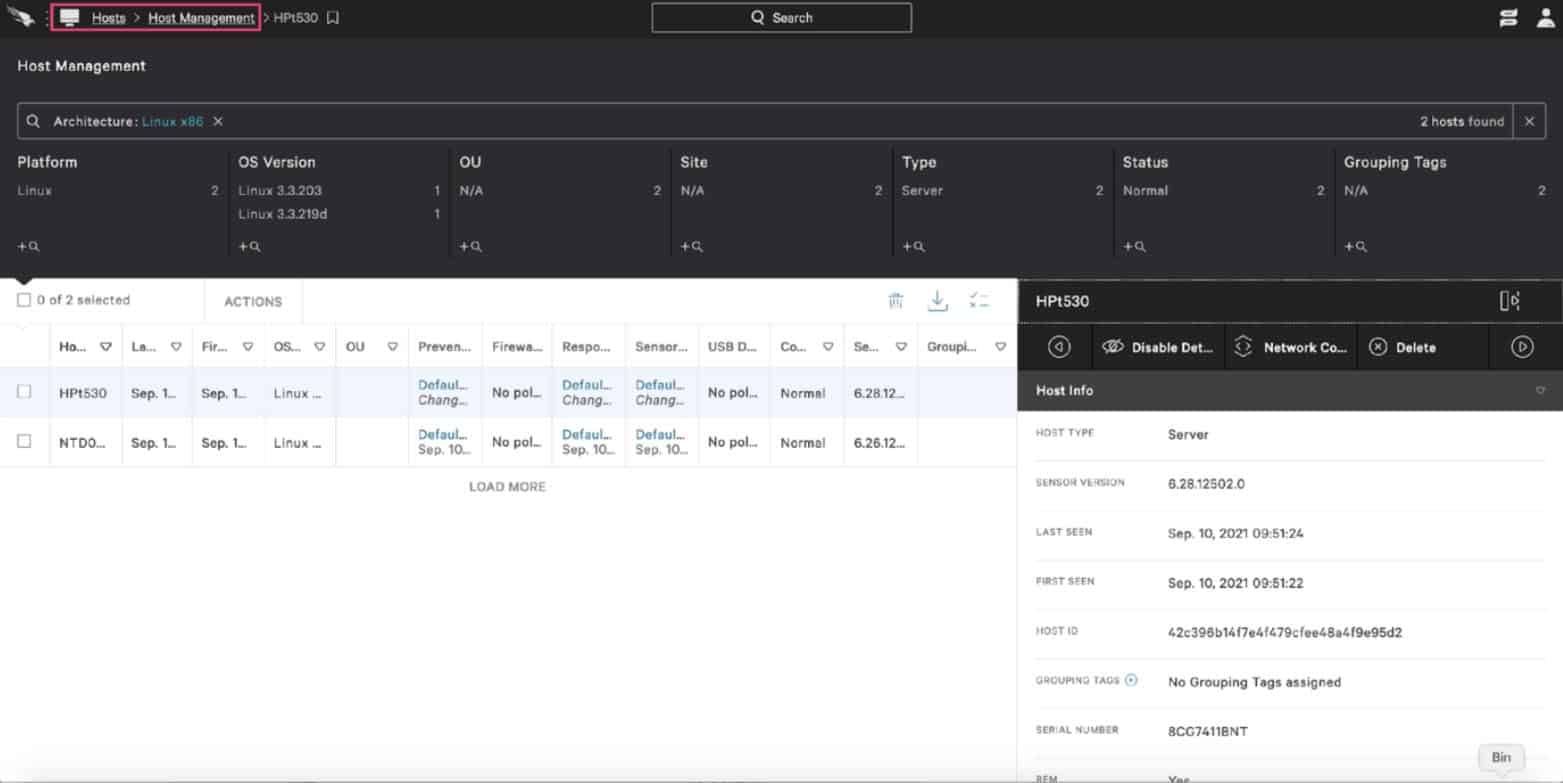
You can then drill down further into the Linux Host Management, and into the devices.
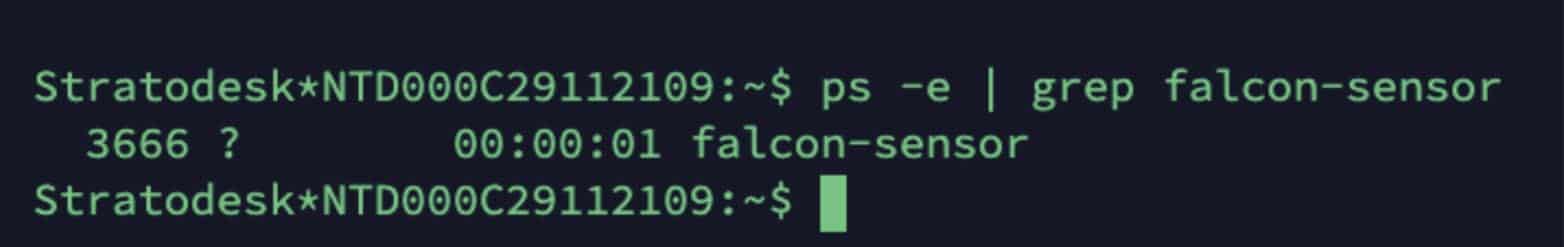
If you are still unsure if the falcon-sensor service is running, then you can ssh on the endpoint and run the following command:
ps -e | grep falcon-sensor
You should see an output like the one below, which means the service is running.
 Summary
Summary
Other than the configuration directly, Stratdesk NoTouch OS is a centrally managed secure, read only Linux operating system. For those customers who require to add extra layers of security then it’s possible to add disk encryption with a user input password that also prevents unauthorised access to the OS.
For those customers who also require a cloud based anti-virus solution then there’s also the option of deploying Crowdstrike via the Extension Module feature so that you can monitor and track any potential threats in real time.